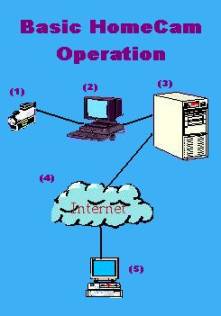
UNIX Operating System Characteristics
by Rebecca Orton
for Operating Systems class
taught by Professor Wayne
UNIX System
The characteristics covered in the UNIX system are process management, interprocess communication, memory management and CPU scheduling, secondary storage management, input/output management, and file management.
Process Management
When the kernel copies a program into memory and begins its execution, this executing program is called a process. A distinction is made between a program that is kept in a file on the disk and a process that is in memory. (Kochan and Wood, 1985, pg. 43). A process is represented by a process structure and a user structure (U structure) (S ilberschatz and Peterson, 1988, pg. 507). These are the two data structures under the control of the kernel that are used to store information about a process. The information stored in the process table includes the process identifier (pid), user-id, the size of the process, the location, and whether the process is swapped in or out. When a process is in primary storage it has its u structure with it. The u structure contains information about the process that is needed only when the process is resident or swapped in. The u structure stores the user—id used for file access, and the registers that are saved when the process is blocked (Keller, 1988, pg. 229).
A new process is produced by the fork call. The fork call creates two almost identical process with the same variables and values (Silberschatz and Peterson, 1988, pg. 472). The fork call allocates a new process structure with a new pid for the child process and the u structure is copied (Silberschatz and Peterson, 1988, pg. 481). But parent and child processes do not share their memory (Keller, 1988, pg. 236).
The exec call is used to replace the current process with a different process (Kochan and Wood, 1985, pg. 244). The exec call initiates execution of the process along with its arguments. Unlike other commands that are executed as new processes, the exec call doesn’t create a new process. Once the exec call starts execution, there is no return to the process that initiated the exec call (Kochan and Wood, 1985, pg. 368). The exec call doesn’t create a new process structure or u structure, rather the executable text and data of the process are replaced (Silberschatz and Peterson, 1988, pg. 482). Both parent and child processes continue execution at the instruction after the fork call with only one difference. The return code for the fork call is zero for the child process, and the pid of the child is returned to the parent (Silberschatz and Peterson, 1988, pg. 472) Memory is allocated to the child process. If the child process grows and there is insufficient memory available, then memory large enough to contain the expanding process is allocated by using a first—fit strategy. If there is none, then secondary storage is allocated, and the process is swapped out. The process will be swapped in when enough memory becomes available again (Keller, 1988, pg. 236).
A process may terminate by using the exit call. Its parent process may wait for that event by using the wait call (Silberschatz and Peterson, 1988, pg. 473). A waiting parent process is notified by the exit call in the child process that the child has finished (Keller, 1988, pg. 237). When a process completes execution, it returns an exit status. The exit status is an integer indicating whether or not the process successfully ran. An exit status of zero indicates that a process succeeded, and a nonzero status indicates that it failed. The execution of the exit call causes the current process to be immediately terminated (Kochan and Wood, 1985, pg. 369). The wait call causes the suspension of a process until the process finished executing. If the process waited for is not specified, then the process waits for all child processes to finish executing (Kochan and Wood, 1985, pg. 384).
All user processes are descendants of one original process, mit with the pid of 1 (Silberschatz and Peterson, 1988, pg. 473). The main process is the shell. The shell major responsibilities are process execution, environment control, and pipelines (Kochan and Wood, 1985, pg. 46). The kernel is hidden by the shell that surrounds it. The kernel’s major responsibilities are process management, input/output management, and file management (Keller, 1988, pg. 228). A subshell is an new shell that is executed by the login shell in order to run a process. Whenever a new shell runs, it runs in its own environment, with its own set of local variables (Kochan and Wood, 1985, pg. 222). If the command line sequence is terminated by an ampersand character “&“ before the end of line character, then the process is run asynchronously in the background. The process number is displayed at the terminal when this is entered (Kochan and Wood, 1985, pg. 357).
Interprocess Communication
Two processes can only communicate with each other through temporary files or by knowing beforehand each other’s pid. Pids are allocated sequentially starting at 1 at system startup. The control structures in the operating system are tree structured so that there is limited communication up and down the tree, from parent to child and vice versa (Keller, 1988, pg. 242). Signals are like software interrupts. They inform a process that an error occurred, and most can be ignored (Keller, 1988, pg. 237).
Pipes is another form of communication between processes. They may be created before the fork call, and the endpoints are then set up between the fork process and the exec process (Silberschatz and Peterson, 1988, pg. 473). A pipe accepts data from another process as they are produced. The pipe is a sink into which data is sent for processing. Data written into one end of the pipe is read from the other end. The synchronization, scheduling, and buffering of pipes are handled automatically (Keller. pg. 214). A pipe can be considered as a reliable unidirectional byte stream between two processes (Silberschatz and Peterson, 1988, pg. 501). Pipes process data in FIFO order while the process that initiated the pipe continues execution and production of data (Keller, pg. 145). A pipeline is essentially queues of bytes between processes (Silberschatz and Peterson, 1988, pg. 473). The pipe connects the standard output of one process to the standard input of another process (Keller, 1988, pg. 214). In a pipeline, the exit status comes from the last command in the pipe (Kochan and Wood, 1985, pg. 142). A pipe is an open file with a fixed size connecting two processes and is accessed by a file descriptor, like an ordinary file (Silberschatz and Peterson, 1988, pg. 473). It is implemented as an ordinary file, with the following exceptions. There is no permanent name in the file system, when it is created by the pipe call. If the pipeline was interrupted abnormally, temporary files with the extension of $$$ might be found in the file system. If a process attempts to write to a full pipe, the process is suspended. Once all data previously written into the pipe is read out, then writing continues at the beginning of the file. Pipes are not really true circular buffers (Silberschatz and Peterson, 1988, pg. 501). A filter which is related to pipes, reads the standard input, selects from it or modifies it and passes the output as standard output (Keller, pg. 215).
Memory Management and CPU scheduling
Memory management is a first fit variable partition strategy with swapping. Other systems may have sophisticated algorithms for dealing with memory problems, but Unix just does a controlled crash, and tries instead to prevent problems (Silberschatz and Peterson, 1988, pg. 467-468). Pre—virtual memory systems used swapping solely to handle memory contention. Without virtual memory, a process larger than than non—kernel main memory cannot be run at all (Silberschatz and Peterson, 1988, pg. 484). Many USG systems, particularly System V, currently use the swapping scheme. Berkeley systems rely on paging for memory contention management and only rely secondarily on swapping (Silberschatz and Peterson, 1988, pg. 485).
CPU scheduling is a combined priority and round-robin strategy with dynamically computed priorities. Processes are given small time quantums by a priority algorithm. For CPU bound processes, scheduling reduces to round—robin (Silberschatz and Peterson, 1988, pg. 507). CPU scheduling benefits interactive processes (Silberschatz and Peterson, 1988, pg. 482), and CPU bound processes can fill the gabs created by the input/output bound processes (Keller, 1988, pg. 235). Every process has a scheduling priority, and large numbers are low priority. Processes doing disk input/output have negative priorities and cannot be killed by signals. The more CPU time a process accumulates, the more positive its priority becomes. Negative feedback makes it difficult for a process to take over the CPU. There is no preemption of one process by another, and aging is used to prevent individual starvation. Newer systems use a 1/10th of a second time quantum while earlier ones use a full second (Silberschatz and Peterson, 1988, pg. 482—483).
If there is too much contention, processes are swapped out until enough memory is available. The system data segment includes the u structure and the kernel stack. The user data segment includes non—sharable pure text, data and the stack. Both the u structure and the user data segment are swapped in together (Keller, 1988, pg. 229). All of these are kept in contiguous memory to keep swapping efficient but some serious external fragmentation of memory may result. A sharable text segment does not have to be swapped out, because it is read—only, nor does a sharable text segment have to be swapped in for a process when another instance is already in memory. Less swap traffic results, and is one of the main reasons for keeping track of sharable text segments. Another reason is the smaller amount of memory needed for multiple processes using the same text segments (Silberschatz and Peterson, 1988, pg. 484—485). When a process executes read—only code, reentrant code, or sharable pure text, a text table linked to the process table is used. The process table uses the text table to access a separate memory region containing read—only code (Keller, 1988, pg. 229).
Decisions on which processes to swap in or out are made by the swapper scheduler, process 0. The scheduler checks at least once every four seconds for processes to swap in or out (Silberschatz and Peterson, 1988, pg. 485). The switch between user and kernel modes due to a clock interrupt is a manifestation of context switching. The active process may be suspended or blocked. The active process may have initiated a call such as an input/output request or the scheduler may have required the process to be suspended. Then the active process is suspended, and it is marked as suspended. The current program counter is saved on the stack, and other process data including register contents are saved. Finally, the new program counter address associated with the processing of the input/output request is placed in the current program counter and executed. This sequence is reversed in order to restore the suspended process when the input/output request has been completed by the system (Keller, pg. 232). A process is more likely to be swapped out if it is idle, has been in memory a long time, or has a large size. If no easy victims are found, other processes are picked by age. A process is more likely to be swapped in if it has been swapped out a long time, or has a small size. To prevent endless swapping, a process is not allowed to be swapped out if it has not been in memory for a set amount of time. If there are no current processes to swap out, then the process table is searched for another process that deserves to be brought in. The process picked is determined by how small it is and how long it has been swapped out. If there is not enough memory available for the picked process, processes are swapped out until there is (Silberschatz and Peterson, 1988, pg. 485).
When a process decides to release the CPU, it goes to sleep on an event. The sleep call is used. It takes as an argument the address of a kernel structure related to an event that the process wants to wakeup on (Silberschatz and Peterson, 1988, pg. 483). The event being waited for is noted in the process table (Keller, 1988, pg. 235). When a kernel process is suspended, the reason for its suspension is stored in the process table, coded as an integer. This integer then represents an event. The event uses the kernel stack of the system process currently executing, and that system process is responsible for waking up the suspended processes for that event.
When the event occurs, the system process involved issues the wakeup call which takes as an argument the address corresponding to the event (Silberschatz and Peterson, 1988, pg. 483). Then the process table is searched for processes waiting for that event (Keller, 1988, pg. 238). All the processes sleeping on the same address are put the ready queue. But the scheduler picks the process that actually does run. The sleep call also takes as a second argument the scheduling priority. If the priority argument is negative then the sleep call also prevents the process from being prematurely awakened by an exceptional event, such as signal. If a process decides to sleep on an event on account of a flag that it checked, for example, and the event occurs before the process can execute the sleep call, then the process may sleep forever. Raising the hardware processor priority during the processes’ critical section prevents processes from sleeping forever. No events can occur, and only the process desiring the event can run until it is sleeping. The hardware processor priority is used to protect critical regions throughout the kernel and causes the most difficulty in moving Unix to machines with multiple processors (Silberschatz and Peterson, 1988, pg. 483—484).
Secondary Storage Management
Direct access and sequential access are supported through system calls (Silberschatz and Peterson, 1988, pg. 507). The file system is a directed graph, specifically a hierarchical tree structure (Keller, 1988, pg. 218). Each of the nodes in the tree is called an mode, which is a file definition. The modes on the disk contain a number of block addresses for accessing a file, including a indirect address, one double indirect address, and yet another triple indirect address (Keller, 1988, pg. 220). The kernel uses a logical device and a mode number pair to identify a file. The logical device number defines the file system involved. A bit used in the mode structure indicates if the mode has a mounted file system. The mode structure is an in—core copy of the mode on the disk. A reference to a file causes a search through the mount table to find the device number of the mounted device. The device number is used to find the mode of the root directory of the mounted file system~ Finally that mode is used to find the file. The actual number of file systems on a drive varies according to the size of the disk. The purpose of the computer system as a whole is also considered, for example whether it is single user or multi—user. The root file system is always available. Others may be mounted or in other words, integrated into the directory hierarchy of the root file system (Silberschatz and Peterson, 1988, pg. 492).
The disk on which the files reside is structured with a boot block, superblock, mode list, and the data blocks (Keller, 1988, pg. 220). The super-block contains the file system header and the static parameters of the file system, for example the free space parameters. The superblock also includes the total size of the file system, the number of modes, and the block size of the data blocks. The superbiock of each mounted file system is kept in memory for accessing speed. For example, every 30 seconds, the super-block is written to disk, to keep the in-core and disk copies synchronized. This is done by using the sync call. When system or hardware bugs destroy the in—core superblock during a system crash then the free block list is lost. The recovery of the free block linked list accessed by the superbiock is difficult because it requires a long examination of all blocks in the file system (Silberschatz and Peterson, 1988, pg. 493-495).
Input/Output Management
The details of input/output devices are hidden from the rest of the kernel. The input/output system consists of buffer caching, general device driver code, and specific drivers for hardware devices. The device drivers are the implementation of the details of specific devices (Silberschatz and Peterson, 1988, pg. 496—497). The devices are accessed using special device files within the file system (Keller, 1988, pg. 218). A special file is an interface between processes and the kernel. Each device is connected to a special file (Keller, 1988, pg. 219). modes are associated with special files. The major and minor device numbers, and the class are stored in the mode (Keller, 1988, pg. 225). Device drivers are accessed by one of two arrays or tables of entry points. One is for block devices, and the other is for character devices. The major device number is used as an index to find an entry into the appropriate device driver (Silberschatz and Peterson, 1988, pg. 497-498). The minor device number selects a device out of a group of identical physical devices (Keller, 1988, pg. 226). It is used by the device driver to interpret a device. A device driver module is connected to the rest of the kernel only by the entry points, and by the use of the common buffering systems. This separation of device drivers is an aid to portability and configuration (Silberschatz and Peterson, 1988, pg. 498). The entry point tables contain pointers used to access the buffers for devices. Buffers are not permanently assigned but are allocated as needed from a pool of empty buffers. For block devices, there is in the block table code, routines for optimizing reads and writes (Keller, 1988, pg. 226).
The block buffer cache consists of buffer headers, each of which points to a piece of physical memory as well as a device number and a block number on the device. The buffer headers are kept in linked lists. The buffers in these lists are hashed by device and block number to make searches efficient. When a block is wanted from a device during a read, the cache is searched first. If the block is found, then it is used and input/output transfer becomes unnecessary. If the block isn’t found, a buffer is picked from the list of empty buffers. Then the device and block numbers associated with the empty buffer are updated, memory is found for it, and new data is transferred into it from the device. If there are no empty buffers, the least recently used buffer is written to its device and then it is used. On a write, if the block is already in the buffer cache, the new data is written to the buffer. The buffer header is marked to indicate the buffer has been modified, and that input/output doesn’t have to be done immediately. The data will be written when the buffer is selected again for different data. If the block is not found in the buffer cache, an empty buffer is picked the same way as with a read operation and data is transferred to the buffer. Writes are forced for dirty buffer blocks once in a while in order to minimize potential inconsistencies in the file system if a system crash occurs (Silberschatz and Peterson, 1988, pg. 498).
Some devices, such as magnetic tapes, require blocks to be written in sequential order, so synchronous writes of buffers to these devices are forced. Directory blocks are also written synchronously. When data from a disk file is read, some read— ahead occurs, but reads are closer to asynchronous than writes (Silberschatz and Peterson, 1988, pg. 499). Read-ahead usually keep the buffers filled. Writing is often delayed and results in less physical input/output. A system crash may result in the loss of data in the buffers that have not been transferred physically even though the processes associated with the data may have terminated (Keller, 1988, pg. 225). The sync call is used to start flushing all the buffers out.
The terminal is the standard input, output, and error (Kochan and Wood, pg. 33). Terminal drivers use character buffers (Silberschatz and Peterson, 1988, pg. 500). C-lists are buffers smaller than those of the block buffer cache (Silberschatz and Peterson, 1988, pg. 497) and the blocks of characters are kept in linked links. A write call to a terminal puts characters on a queue for the device. An transfer is initiated, and interrupts cause the outputting to the device of characters from the queue. Further transfers occur on subsequent interrupts. Input is similarly interrupt driven as well (Silberschatz and Peterson, 1988, pg. 500). Terminal input/output differs from other character input/output in that some preprocessing of the queue occurs. For example erase editing to incorporate changes the user has made during the time the line was entered is performed (Keller, 1988, pg. 225). Terminal drivers support two input queues, and conversion from the raw queue to the canonical queue is triggered by an end of line character on the raw queue (Silberschatz and Peterson, 1988, pg. 500).
File Management
All files are defined to be simply a stream of bytes and each byte is individually addressable by its offset from the start of the file. Since the logical record is one byte, the file system automatically packs and unpacks bytes into physical disk blocks (Silberschatz and Peterson, 1988, pg. 351). A file has no intrinsic structure, and the user is the one that imposes a structure on it, if any. An Unix file uses less space than a file in a file system that stores fixed length records because space is not wasted by filled-in blanks. Time is used to keep a count of the number of characters processed in variable — length records. Unix’s general purpose process tools would be more difficult to implement if the files existed in a variety of forms (Keller, 1988, pg. 218).
Access to a file can be given at three levels of permission: read (r), write (w), and execute (x) (Keller, 1988, pg. 219). For the file permissions, a domain such as owner, group, and public, is associated with the user. Domain switching is when the user identification is changed temporarily. Associated with each file are an owner identification and domain bit (Silberschatz and Peterson, 1988, pg. 394-395). When a user “Albert” with a userid “A” starts executing a file owned by “Barry” with a user-id of “B”, the user-id of “Albert” is set to “B”,provided that the associated domain bit of “Barry’s” file set to on. After the file finished executing, then “Albert’s” user-id is reset to “A”. There are actually two user identifiers used by the kernel. The effective user identifier is the identifier used in determining file access permissions. The real user identifier is left alone. This allows certain processes like mail to have higher privileges while still being executable by users (Silberschatz and Peterson, 1988, pg. 473).
There are both absolute pathnames and relative pathnames. Absolute pathnames start at the root directory of the file system and are distinguished by a slash at the beginning of the pathname. Relative pathnames begin in the current directory and is an attribute carried within the process accessing the pathnaine (Silberschatz and Peterson, 1988, pg. 470). Always associated with each user of the system is a home directory. When a user logs into the system, the user is placed automatically into the home directory (Kochan and Wood, 1985, pg. 10). The user refers to a file through the pathname, while the file system refers to the file definition through the mode. A file may be known by more than one name in more than one directory. Such multiply names are known as links and all links are treated equally (Silberschatz and Peterson, 1988, pg. 470). An empty directory at any level can be replaced by a new branch corresponding to the files on a newly mounted disk volume. Once the volume is incorporated into the file system, its physical identity is lost. To find out where files actually reside is difficult and file system cross-linkings are prohibited as a result (Keller, 1988, pg. 219).
The kernel maps the pathnaine to an mode through the directories (Silberschatz and Peterson, 1988, pg. 491). Directories are files and can be recorded in other directories higher up in the file system (Keller, pg. 215). A directory contains only the filename and a reference number. More detailed information is contained in the mode for a file, such as user—id, protection status, disk block addresses where the file is stored, file size, and other information. Inodes are stored in i—lists and the offset of the modes from the start of the i-list is the modes’ i—number, which is the reference number stored in the directory (Keller, 1988, pg. 220).
When a file is opened during a open call, the file’s mode is fetched and placed in the system mode table. A pointer to the mode is placed in the allocated file structure. A second pointer to the mode is placed in the system file table. Finally, a third pointer to the entry of the system file table is placed in the u structure for the process. The system file table holds the file pointer because the file pointer of a sharable file cannot reside in the mode table nor in the open file section of the process table (Keller, 1988, pg. 223). In other words, the file descriptors refer to the file structures (Silberschatz and Peterson, 1988, pg. 491). The file descriptors are the reference numbers of the files in the system file table. The entries in the system table contain pointers to the corresponding modes for the files in the system mode table (Keller, 1988, pg. 222). The file descriptors index a open file table for the current processes in the process table. The entries in the open file table contain pointers to file structures. The file structures contain pointers to the modes (Silberschatz and Peterson, 1988, pg. 491). The file structures contain the offsets. File structures are inherited by the child process after a fork, so some processes may have the same offset into a file. The mode structures pointed to by the file structures are allocated out of a fixed — length table. The in—core modes have a few extra fields, namely a reference count of how many file structures are pointing at it. The file structures have a similar reference count for how many modes refer to it (Silberschatz and Peterson, 1988, pg. 491—492).
The locations of specific files and directories in the file system have been defined by programmers, but the kernel actually depends only on the existence of the directory /etc/init, which is used to initialize terminal processes (Silberschatz and Peterson, 1988, pg. 470). The root directory contains special purpose subdirectories called dev, bin, lib, etc, tmp and usr. The dev subdirectory is for special files for devices. The bin subdirectory is for executable utility programs. The lib subdirectory is for libraries of system utilities, the etc subdirectory is for restricted system data, for example the algorithmic password file resides here. The tmp subdirectory is for temporary files used by the system utilities, and the usr directory contains all the user subdirectories, and other less used subdirectories such as bin, tmp, dict which contains wordlists and spell checkers, and the man subdirectory which contains the full Unix programmer’s manual text files (Keller, 1988, pg. 216). Files can be created, opened, read, written, closed, and unlinked. For manipulating device parameters, there is an additional system call, ioctl, standing for input/output control (Silberschatz and Peterson, 1988, pg. 472).
In summary, the Unix system uses swapping and priorities with round robin scheduling to manage parent and child processes, even though there is limited interprocess communications. The management of secondary storage, input/output, and files are interrelated and even combined. The conclusion of the Unix system characteristics is that it is flexible and generic, perfect for programmers.
References
Keller, Laurie S. Communicating with and Controlling the Computer . New York, London, Toronto, Sydney, Tokyo: Prentice Hall International Ltd., 1988.
Kochan, Stephen G., and Patrick H. Wood. Unix Shell Programming. Hasbrouck Heights, NJ, Berkeley, CA: Hayden Book Company, 1985.
Silberchatz, Abraham, and James L. Peterson. Operating System Concepts. Reading, MA, Menlo Park, CA, New York, Don Mills, Ontario, Wokingham, England, Amsterdam, Bonn, Sydney, Singapore, Tokyo, Madrid, San Juan: Addison-Wesley Publishing Company, 1988.
Citizen's Tree Rescue
History
Citizens Tree
Rescue winter/spring 2001 campaign.
Summary
Nov. 2000 A&B Landscaping and Tree Service is awarded a contract to prune Oak
Park parkway trees. It is the lowest bid by a substantial amount. A&B's price
to prune 8-15 inch diameter trees is $19.00 a tree, compared to $25, $29, $39
and $60 for the other 4 bids. A & B did not furnish the required number of 4
references from other satisfied municipalities.

|
Jan.
2001 A&B begins severe pruning at Austin Blvd., between Madison St. and
South Blvd., leaving deformed trees as it moves westward. Hundreds of
complaints flood Village Hall and continue until the pruning is stopped
in April.
Feb.
2001 Urgent requests by local landscape architects to meet with Public
Works director Joe Euclide, to whom the forestry department reports, are
ignored.
March
2001 A request to the Village board by residents for a moratorium on the
pruning to assess the severity of the pruning is ignored. Residents confront
the forester and contractor crews in the street, actions which play out
in the press. Finally, the Village agrees to meet with residents and their
representative, nationally-known urban forester Chuck Stewart.
|
Narrative
A Village
contractor, A&B Landscape and Tree Service of Riverside, Illinois, began pruning
Oak Park's parkway trees in January 2001. On March 9, resident Kathryn Jonas
met with Forester Jim Semelka to express concerns over the severity of the pruning
that violated Village pruning standards east of East Avenue between Madison
St. and South Blvd., which he defended as necessary. Meanwhile, repeated requests,
since February, by other concerned residents, including landscape architect
Carol Yetken, to meet with Semelka's supervisor, Public Works director Joe Euclide,
were being ignored. The combination of these events and the urgency to halt
the block-by-block severe pruning prompted this letter to the editor.
This essay
appeared in the March 21, 2001, Oak Leaves in slightly different form:
Pruning
is destroying trees' character
By Kathryn Jonas and Gary Johnson
OPEN LETTER
TO THE VILLAGE OF OAK PARK PRESIDENT BARBARA FURLONG, TRUSTEES AND TRUSTEE CANDIDATES
Let it be known that there is a groundswell of discontent in the village over
the current pruning of parkway trees. A Village contractor has been systematically
stemming up trees twenty feet and higher, (the village specification is 14 feet)
destroying their character by turning them into palm trees, and in some instances
causing irrevocable damage. Professionals we have consulted say they are removing
up to 50% of the foliage, which can significantly reduce the life span of a
tree. In a matter of minutes, with their chain saws and pole pruners, they are
destroying what has taken twenty-five years and more to grow.
We urge you
to drive down the 200 S. block of Humphrey, the 100 S. block of Harvey or Elmwood
or Scoville, for example, and see the destruction of once beautiful lindens,
ginkgoes, ashes, oaks and hackberrys. (The area is bounded by Austin-Oak Park,
South-Madison.) Get out of your car, take a walk, ring a few doorbells and talk
to the residents, the taxpayers. There is a lot of anger and hurt, disbelief
and dismay at was is happening. Take Carol Buer on Harvey Ave. She calls the
pruning "ridiculous," "absurd," "tragic." She works in the Rehabilitation field.
"And now I have to come home and look at stumps?" She says she's 48 years old
and will never again in her life time see a mature healthy tree in east Oak
Park.
 |
Our
gut reaction to blame the contractor changed after we talked to Village
forester Jim Semelka, who defends his methods. Public works director Joe
Euclide, Semelka's boss, turned down our request for a pruning moratorium.
The forestry commission told us, "We'll get back to you in a month."
Last
week, we invited certified arborist Chuck Stewart, a nationally respected
urban forester with nearly 40 years experience in the forestry field,
and who consults with the Arbor Day Foundation, to view our trees. He
called the pruning job "pathetic," "horrible." Mr. Stewart rescued the
Village from a tree pruning debacle 13 years ago at our urging, when a
number of elms along Jackson Blvd. were felled into install a major water
main.
Back
then, it was citizen action that stopped that assault on our trees. Mr.
Stewart says the natural form or our trees is being destroyed. The cutting
off of all lower branches while leaving a carrot top of foliage actually
invites storm damage. The skinning of all small branches leaving tufts
at the tips (called "lions-tailing" in the industry) weakens limbs.
|
The severity
of the pruning, he says, is something that would be done to trees on an eight
or ten year pruning cycle, not a four year plan the Village cites as its goal.
A second certified arborist, (who wishes to remain anonymous) told us the severe
pruning has reduced the life span of our trees. What's left of the foliage will
simply not be able to support the extensive root system.
In fact, the
village is violating four of the seven ANSI (American National Standards Institute)
A300 pruning Standards for Tree Care adopted by the Illinois Arborist Association,
the National Arborist Association, and the International Society of Arborists.
1) "To obtain the defined objective, the growth cycles and structure of the
individual species...should be considered."
2) "Not more than 25% of the foliage should be removed within an annual growing
season...the percentage and distribution of foliage to be removed shall be adjusted
to the plants species, age, health and site."
3) "Not more than 25% of a branch or limb should be removed when it is cut back
to a lateral."
4) "...lion's tailing [skinning of all leaves and stems] shall be considered
unacceptable pruning practices for trees."
How long
can this misguided program proceed before everything is lost? To watch A & B
Landscaping tear through an entire block in an afternoon, hacking away sometimes
50% of any given tree, is staggering. Is A & B qualified for the job? Why hasn't
Oak Park adopted the pruning standards generally accepted in the industry? Why
are the village specifications of 14 ft. clearance not being enforced?
For prospective,
we urge you look at an area in Park Ridge were pruning has just been completed
on a 6 year pruning cycle. (Between Devon-Touhy, Dee-Greenwood) The difference
between what that village is doing and what Oak Park is doing is startling.
The pruning cuts are scarcely noticeable, and they are carefully made to preserve
the structure of the tree. You can quickly identify each of the species. They
are not limbed up beyond recognition. The only place in Oak Park that looks
like Park Ridge are the neighborhoods that have yet to be pruned!
Dear Village
board president and trustees, realize that one-sixth of our trees have been
chopped, skinned and disfigured, their health and vigor compromised. Therefore,
we are petitioning you, our elected officials, to declare an immediate moratorium
to evaluate the current pruning program by outside experts approved by concerned
residents.
Article, Wednesday
Journal, March 21, 2001
Wide lawns, narrow trees
by Rebecca Little
Members of
the Citizens Tree Rescue are calling their trees "toothpicks," "palm trees,"
"telephone poles," and "amputees" since the village has stated pruning the parkway
trees in the square between Austin Boulevard and Harlem Avenue, and South Boulevard
and Madison Street.
Gary Johnson
and Kathryn Jonas started the Citizens Tree Rescue when they heard their neighbors
were also unhappy with the "hack job."
The village
has hired A&B Landscape and Tree Service to prune the lower branches of all
trees. No branches are to be below 16 feet or, in some cases up to 25 feet from
the ground. The policy is uniform for all trees on the parkway.
"I am very
concerned that the severity of the pruning is not only having a huge negative
impact on the beauty of our streetscape, but most importantly, not consistent
with accepted horticultural standards for parkway tree pruning," Jonas said.
Jonas and
Johnson, who live on the 100 block of South East Avenue, have requested a moratorium
on the pruning until an arborist can submit a report to the village.
Jonas attended
a village Forestry Commission meeting last week to request the moratorium with
village Forester Jim Semelka, Public Works Director Joe Euclide, and the trustees.
"They said they would take it under consideration and get back to me in a month.
In a month, it will be finished."
Euclide turned
down the moratorium, but Jonas had a meeting with village president Barbara
Furlong, Semelka and Euclide this morning. The result was not available at press
time. Semelka drove around the neighborhood with Jonas, but he and Euclide maintain
the contractor is pruning the trees acceptably and according to contract.
|
The
village pruning specifications to remove limbs below 14 feet from ground
level. The village is pruning more so that the contractors will not have
to return in a long time.
"The
whole rationale is that they haven't been pruned in a long time, so they
must do a severe job," said Karen Heller, who works at Carol JH Yetken,
Landscape Architects. "That's like saying I haven't had a haircut in a
long time so I'm going to get a crew cut."
A&B
is encountering angry and protesting residents as they proceed down the
blocks. On March 19, worked rolled their trucks up to some of the oldest
trees in the village, on the 100 and 200 blocks of South Euclid, hoping
to trim branches.
|

|
"George Schneider
of the 100 block of South Euclid called the workers "hired thugs."
"These guys
must get paid for the number of woodchips they get," Schneider said sarcastically.
Leslie Wilson
of the 200 block stated, "People choose to live here because of the forestry.
I don't want to live in a concrete jungle. Wait until the leaves grow back and
the neighbors see what they've got left."
The Citizens
Tree Rescue has called in arborist Chuck Stewart, who called the job "pathetic."
Stewart consulted for the village some 10 years ago during the uproar following
the DuPage County water commission's extensive pruning of trees along Jackson
Boulevard. That cutting was done to allow access for equipment necessary in
constructing a huge water main connecting Lake Michigan to DuPage County.
"A lot of
people are upset about this," Johnson said. "But the village heard 'tree hugger'
and writes it off."
Landscape
architect Carol Yetken has a meeting with Euclide next week to discuss what
she calls "misshapen trees."
"I think they
are pruning too much and to severely for these trees, particularly those that
are younger, 25 to 30 years old. There seems to be an arbitrary principal that
no matter what type of tree, size, width of the parkway, they are all cut to
a certain height."
Yetken said
lindens and maples have lower branches, and should not be cut to an elm standard.
The trees
are left with a tuft of leaves at the top, which Johnson said is dangerous during
storms, and there may not be enough leaves support the root system.

|
"I understand
some pruning is necessary on the street side. But do trees have to be
pruned up to 25 feet on the pedestrian side?" asked Carol Buer, a resident
of the 200 block of South Harvey Avenue. "We all feel like dwarves now
when we walk down the street."
"They
are ignoring the ornamental aspects of trees, and losing the character
of the individual trees," said Mark Finger, a landscape architect at Yetken's
firm. "This is irreversible, it's blitzkrieg. We want so acknowledgment
that this can't be an acceptable routine."
Tito
Cantiliano of A&B Landscape & Tree Service had little to add.
"We
are supposed to trim the trees up to 16 feet. The village is paying us
to do this."
"Just
drive around the neighborhood. See for yourself," Johnson said.
--Christopher
Decker contributed to this report.
|
Article, Oak
Leaves, March 21, 2001
Residents bark at OP over tree trimming
by Cheri Bentrup
Resident
have been stepping up their efforts to thwart the village's tree-trimming by
taking their concerns to the Oak Park Forestry Commission and gathering in the
streets to stop the trimming.
Several resident
on the 200 block of Euclid Avenue came out of their houses Monday morning to
question the trimming methods of the village-hired contractor, A&B Landscaping
Tree Service of Riverside.
"I've been
watching it since they started butchering trees," Leslie Wilson said of the
gingko tree in her parkway.
Neighbor
Sandy Heitzman said she yelled at a tree-trimmer to get out of the linden in
her parkway.
"There was
no reason for him to be trimming up there," she said, noting that he was up
high in the treetop. "This was a fortuitous day I was home late."
|
"I've
never seen this kind of thing. I makes you wonder if they're getting paid
by the truck," added neighbor Judy Shepelak.
Oak
Park Forestry Supervisor Jim Semelka, who stood alongside residents Monday
as crews trimmed parkway trees, maintains the trees are being trimmed
properly.
|
 |
"I understand
their aesthetic concerns," Semelka said, "but I don't think they're taking too
much off.
"The trees
look stark after trimming because, Semelka said, crews are making up for years
of missed pruning.
"I understand
their concerns and I'm with them," said landscaping firm co-owner A. J. Ruska.
"We're trying to catch up for years of (not) doing them. We're doing a structured
pruning so in four years all we'll have to do is maintenance.
"It would
behoove me to do less because it would go faster," Ruska said. "I am a lover
of trees, too."
Crews have
been trimming from South Boulevard to Madison Street, starting along Austin
Boulevard and working their way west to Harlem. Early this week, they were on
Euclid. Kathryn Jonas, a resident of the 100 block of South East Avenue, attended
last week's Forestry Commission meeting and asked that tree trimming be stopped
until the pruning standards could be reviewed.
"We look like
we're in Florida; they look like palm trees," she said of the recent trimmed
trees.
Jonas,
who has worked in the landscaping industry for 17 years, thinks the excessive
trimming could be endangering the trees' health.
"I think there
are some valid concerns here," she added. Jonas was told the commission would
take her comments under consideration and discuss them at their April meeting.
"Because
of the situation, I'm requesting a response earlier than that," she said, noting
that the trimming could be done by then.
On March
21, after nearly two months of stalling, and the severe pruning of some 50 square
blocks of trees, the Village finally agreed to a meeting, as detailed by resident
Kathryn Jonas in the summary below.
This summarizes
my recollection of the matters discussed at the meeting, since no one was asked
to take minutes.
Summary
of March 21, 2001, tree-pruning meeting at Oak Park Public Works with the following
people present:
Village President-Barbara Furlong
Village Trustee- Rick Kuner
Assistant Village Manager-Ray Wiggins
Public Works Director- Joe Euclide
Forestry Director- Jim Semelka
Forestry Employee- Pat Cassin
Residents: Mark Finger, landscape architect with Carol H. Yetken & Associates
Karen Heller, landscape architect with Carol H. Yetken & Associates
Mike Elsner- landscape architect with a Chicago firm
Kathryn Jonas- landscape manager with 17 years experience with the landscape/forestry
industry
Chuck Stewart- Consulting Urban Forester with Arbor Day Foundation present at
resident's request.
A meeting
was held at 1:30 p.m. at Public Works at the request of several residents who
have been concerned about the severity of the tree pruning done by the Village
contractor, A&B Landscape and Tree Service, between Austin Blvd. west to Harlem
Ave., between South Blvd. and Madison St.
Mark Finger
and Karen Heller wondered why it had taken so long to get a meeting as Carol
Yetken had requested on five weeks ago when she become aware of the severe pruning.
Kathryn Jonas had previously met with both Jim Semelka, Joe Euclide and the
Forestry Commission to request a temporary moratorium the pruning until the
standards could be evaluated by an independent consultant, but was told that
the pruning was being monitored by the Village and that it was being done correctly.
The residents
and professional landscape architects' specific concerns about the pruning were
the following:
1) The
trees are being limbed up so severely as to destroy the structural characteristics
of the different species.
2) All tree species are being pruned the same way and look like palm trees
or lollipops. They are so misshapen that it is difficult to tell a linden
from a maple, a hackberry or an elm.
3) Stemming up the trees so high (in many cases over 20-25 ft.) is wrong
and irreversible, and is significantly higher than is necessary for vehicle
clearance on the street side or pedestrian clearance on the sidewalk side.
4) Up to 50% of the canopy of the trees is being removed in many cases while
the accepted pruning standards in the industry (ANSI A3000) state that no
more than 25% of the foliage should be removed for the tree's health, and
that removal should be adjusted for the plant's species, age and site, none
of which is being adhered to.
|
 |
5) People
move to Oak Park because it is an older community with mature trees, and the
severe pruning is destroying the beauty of the parkways that are part of the
quality of life in the Village. The shading and visual screening that has taken
twenty years to produce is being destroyed in a manner of minutes.
6) The practice of "lion's tailing," skinning a limb or branch of all side branches
and twigs, leaving a tuft at the end is being done consistently, while this
practice is specifically called out as being unacceptable in the standards.
The Village
forestry department stated that the trees were being trimmed so severely because
there hasn't been a consistent pruning program in the Village for years, so
many of these trees haven't been trimmed for a long time.
Kathryn Jonas
pointed out that the 800 block of Pleasant St. was pruned twice in the 10 years
she lived there, and that pruning has been done throughout the Village over
the last 17 she has lived here. Mike Elsner said that his parkway tree on Harvey
was trimmed severely last year.
Mr. Semelka
also said that the trees were being trimmed so severely because he is trying
to get on a 4 year pruning cycle.
Chuck Stewart
said that was a worthy goal, but that this should call for less severe pruning
this time around if you are going to be back in 4 years.
Mr. Semelka
also said that the Village employees prune all trees under 7" caliper in size,
and that the Village responds to many individual requests by residents to have
the parkway trees pruned in front of their houses. It was suggested by residents
at the meeting that parkway trees are public spaces and that these trees should
be pruned according to accepted industry standards to provide a consistent appearance
on our parkways, and that custom trimming at a homeowner's request was not good
policy.

|
The participants
then walked along the 100 block of Scoville and Elmwood which have recently
been pruned so that residents could point out their specific concerns.
Chuck Stewart noted that the trees were being limbed up much higher than
necessary for 14' clearance on a 4 year trimming cycle. He said that it
didn't appear that the location of the tree (by a street light, at an
intersection, width of parkway) was being considered when making cuts.
He said that too many limbs were being removed for clearance and that
clearance can be better accomplished by removing hanging branches, called
under pruning, than by removing limbs from the trunk.
Mr. Stewart also
said there should be more consistent thinning throughout the tree rather
than cleaning out all lower branches. The meeting ended along the 100
block of East Ave. which had not yet been pruned, and Mr. Stewart gave
specific examples of how the individual trees should be pruned, based
on the species, age and location. Overall, he felt there were not too
many clearance issues.
|
He noted
younger trees under 7" caliper are also being stemmed up too high. He said that
the lower branches on these trees that are not causing clearance problems should
not be cut as they help make the tree stronger, and more storm resistant. Also,
the younger trees should retain as much of their foliage as possible for the
growth of the tree.
It was agreed
that the tree trimmers would start at the 100-200 S. block of Grove St. the
following day as scheduled, adjusting the pruning to take into account the above
matters discussed, and that the Village and residents would look at the trees
before the trimmers proceeded to the next block.
On March
23 Kathryn Jonas sent a letter to Village Board President Barbara Furlong and
Village Manager Carl Swenson confirming the agreements arranged in the March
21 meeting.
Mrs. Barbara Furlong, President, Village of Oak Park
Rick Kuner, Trustee, Village of Oak Park
Mrs. Barbara Ebner, Trustee Liaison to Public Works
Carl Swenson, Village Manager
RE: Street Tree Pruning
We appreciate some of you taking a walk with us on Wednesday (March 210 to look
at the unfortunate results of Oak Park's current tree pruning program, with
grossly incorrect pruning being done both by the Village in-house pruning and
that being done by A & B Landscape. I think it was evident to everyone at the
meeting (except A & B and our own forester) that the beauty and character of
our parkways is being seriously and permanently compromised. We tried to two
weeks to get a meeting with the Village while other like Carol Yetken and Carol
Yetken & Associates tried for 5 weeks to get a meeting. The three local landscape
architects who attended the meeting (Mark Finger, Karen Heller and Michael Elsen)
very strongly voiced their concerns about the misshapened trees both from an
aesthetic point of view and from their long term health. Chuck Stewart, the
well respected national urban forester who rescued Oak Park from the Jackson
Blvd. tree trimming debacle 12 years ago when a water main was installed, was
shocked as to why so much of the trees was being removed on a 4 year cycle.
Less, not more, gets removed on a four year cycle.
Though I
was somewhat encouraged by the resolution of the meeting to monitor block by
block the remaining pruning work, I don't believe this is the right solution
to the problem. It was evident at the meeting that A & B is not qualified to
do the work if they have generated such an uproar and the owner demonstrated
such little understanding of the issues. If he doesn't understand, how does
it get conveyed to the individual crew members? As agreed to at the end of the
meeting, I reviewed the pruning that was done yesterday the 100-200 S. block
of Grove and the 100 S. block of Kenilworth. While less of the trees is being
limbed up, there is still a lot of skinning, instead of thinning in a balanced
way, and many of the larger branch cuts did not need to be made. Look at the
Autumn Purple Ash by the garage on the north side of Pleasant St. just east
of Kenilworth. That pruning job is a good example of removing 50% of the canopy
of a tree and skinning out the branches leaving a tuft of twigs at the tips,
both of which practices are contrary to the standards accepted in the industry,
and detrimental to the health of the tree. We should not have to train our contractor
in the correct manner of pruning trees. They should have never been on the bid
list. My even greater concern is that our own forester has defended these practices
in spite of all our concerns, explaining to Channel 5 crews last night why the
pruning is so drastic.
I request
again a temporary moratorium on the tree pruning in Oak Park by A & B until
they can be properly trained and prove they are capable of following generally
accepted standards. It was clear that we really have no standard. The specification
that Jim (Semelka) gave me reads branches up to 14' should be removed, but he
says what he means is branches should be removed so that in 4 years they are
at 14' height, and then A & B says their instructions were to remove branches
up to 16'. But in reality, many many trees are being limbed up over 20' both
along the street side and the sidewalk side. Soon the trees will leaf out and
the damage will be even more apparent. My question to you is how can we justify
continuing the pruning until this problems permanently resolved by outside experts,
the residents and the Village.
We have spent
considerable personal time on this, for the benefit of the entire town, going
door to door letting residents know that the crews who don't know what they
are doing are approaching their block. We have talked to experts in the field,
looked at other village programs, and come to the conclusion that our forestry
department is not currently qualified to manage the "cherished urban forest"
that Mr. Swenson talked about when he was hired 4 years ago.
Channel
5 television newscast, March 26, 2001.
NBC 5 NEWS 6 p.m.
Newscast March 26, 2001
ANCHOR ALLISON ROSATI:
They're big and beautiful and some residents want to make sure they stay that
way. NBC's Anita Padilla is live in suburban Oak Park tonight to tell us about
a tree fight underway. Anita.
REPORTER PADILLA:
Well, Allison and Mark, anytime you drive through the Village of Oak Park you'll
notice that you're driving pretty much under a canopy of trees. And that is
really what the Village is known for--it's beautiful trees. In fact, they received
several rewards for Tree City U.S.A. But the Village says that these trees are
in severe need of pruning. But residents say its more like a hack job.
TAPE: PADILLA
VOICE OVER Trees are synonymous with the Village of Oak Park. They're everywhere
and on every street. It's been more than a decade since a tree trimming program
was in place. That is, until now. The Village plans to have each tree trimmed
once every four years. And some residents have a problem with the way the work
crews are doing it.
RESIDENT
CHURCH MERYDITH: Although you may want to remove a few low hanging branches
there's no need for this kind of butchery.
RESIDENT CAROL
BUER: This is Tree City U.S.A., yeah. And now it's really become Stick City.
PADILLA: These
folks are angry and say this is no pruning job, but instead a chain saw massacre.
BUER: You
know a weeping willow looks like a linden looks like an ash looks like a ginkgo.
You can't tell. They all look alike. They've all received the same haircuts.
PADILLA: They
want the Village to stop the work until a team of experts can come up with a
better plan. The Village's forestry supervisor says tree trimming is long overdue.
And he says in an urban environment it requires special pruning.
OAK PARK FORESTRY
SUPERVISOR JIM SEMELKA: As this tree is trying to grow horizontally instead
of vertically and in an urban atmosphere you want to promote vertical growth.
One of the reasons is for clearances.
PADILLA:
Now they say another reason they're trimming the limbs sort of near the base
is because they say if a bad storm were to blow through here it would actually
rip that limb off and tear the tree and that would cause the tree more damage.
And that's why their cutting them the way they are. Reporting
live from the Village of Oak Park, Anita Padilla NBC 5 News.
The following
items appeared in the April 4, 2001 Wednesday Journal Viewpoints page
21:
Is the
village pruning or ruining our trees?
Point:
Pruning is good for our trees by Jim Semelka, Oak Park Village Forester
Residents
concerned about the extent of the tree pruning now underway can rest assured
that the trees are in no danger, and will, in fact, be healthier and less likely
to be damaged by high winds, large trucks, disease or insects.
I am pleased
that so many people care so deeply about the trees on the village parkways.
As a certified arborist, I, too, care deeply about trees. However, my professional
training and experience have prepared me to recognize growth problems and take
steps that my seem drastic to the layman, but are in the best interest of the
trees in terms of their long-term health and vitality.
A fresh cut
on a large limb may appear dramatic at first, but I know it will soon heal.
Were that same limb ripped away by a sudden wind or a passing truck, the damage
would be much more lasting, perhaps even life threatening to the tree. And when
these freshly pruned trees leaf over the next several weeks, the positive impact
of the pruning will be clear. Those trees just pruned will produce some of the
most elegant canopies in the Village, allowing easy passage of pedestrians and
vehicles. Even more importantly, these trees will be much less likely to be
damaged in a storm.
While the
pruning may seem extensive, it is based upon sound arboriculture science and
is well within the trees can tolerate. Oak Park's trees deserve nothing but
the best care, and that is what they are receiving.
Counterpoint:
Forestry's pruning program is a hack job by Gary Johnson, Citizens Tree Rescue
An extraordinary
March 21 street meeting of Village officials, nationally-known Urban Forester
and former Oak Parker Chuck Stewart, and citizens concerned about the trimming
of Oak Park trees confirmed what many residents have been screaming about for
months: that this spring's parkway tree pruning by a Village contractor has
been needlessly severe and destructive. Accordingly, Village forestry supervisor
Jim Semelka and a representative of A&B Tree Trimming of Riverside were asked
to change their pruning practices. While standing in the shadows of the severely
pruned trees, the eleven member group, which included Stewart, Village President
Barbara Furlong, Trustee Rick Kuner, Assistant Village Manager Ray Wiggins,
various public works representatives, local landscape architects and concerned
citizens agreed A&B's work would be evaluated on a daily basis for the remaining
blocks (west from Grove to Maple) of the contract. It was also agreed that the
board would get an expert review of the Village's pruning standards before the
next pruning cycle this fall. Semelka and the contractor were called for dismissing
Village and also accepted industry (ANSI) pruning standards, specifically for
1) limbing up trees
significantly higher that the 14 foot standard necessary for vehicle clearance,
2) stripping out too much foliage, and
3) ignoring the characteristics, i.e., species and age, of each tree. Mr. Semelka
was told no one should notice the light touch required of a four year pruning
cycle.
 |
The
next day Mr. Semelka was still spouting his discredited severe pruning
gospel, this time on television to NBC News 5 reporter Anita Padilla,
in a story broadcast on the 6 o'clock news, where disgusted residents
called the pruning "butchering" and "a hack job."
In
letters to the editors, in the Village news letter, and on a continuous
running PR video on the local cable access channel he continues his cant.
If Mr. Semelka's arguments are sound why did the Village, immediately
following the March 21 meeting, hire Chuck Stewart, the concerned citizens'
urban forester, to give two days of training on proper pruning techniques
to the contractor's and the Village's tree crews? Amazing. After three
months of hacking at our trees the guys with the chain saws are finally
getting lessons.
|
It has taken
many weeks to get the attention of Village Hall, which, according to sources,
has been deluged with complaints since January. Promises for citizen meetings
with officials were put off as the Village continually deferred to Semelka.
Calls for a temporary moratorium to evaluate the Village pruning standards were
denied. Indeed, challenges to both Semelka's and the contractor's methods were
met with a mix of arrogance, smooth talk and a patronizing denial that concerned
citizens could ever muster the expertise to recognize something was truly amiss.
Now they have been told by a highly-qualified expert that their practices have
been wrong. They have compromised the health and splendor and the feel of the
street of one-sixth of our urban forest. Oak Park deserves better.
For a stark
visual comparison, drive the 100 south block of Scoville, between Pleasant and
South Blvd., then swing a block west to the 100 south block of East Ave. You
decide which block's trees have been pruned by the guiding hand of urban forester
Chuck Stewart to industry standards. That day, on that block, the crews gathered
small bundles of pruned-out sticks beneath each tree, compared to the tall-as-a-man
brush piles that lined the earlier blocks of massacred trees.
Overall,
while the subsequent pruning, at best, uneven, has improved, one still sees
the disfigured limbing up and cleaning out of foliage that renders some trees
unidentifiable. Concerned citizens now monitor the contractor's crews as they
move into the east-west streets. But the Village crews must still be closely
watched. In what appears to be an isolated case, the 900 and 1000 north blocks
of Euclid have been "hit" by, we assume, the forestry department. Experts also
tell us that forestry department trimmers, responsible for pruning seven-inch
caliper (diameter) and smaller trees throughout the Village, are limbing up
too many of the lower branches that are needed for strong growth. Does anybody
in that department know what's good for our trees?
Oak Park's
Spring 2001 pruning debacle raises many serious questions about the competency
of the Village Forestry Department. The decision by Village Hall to monitor
the trimming of our trees is a victory for the people. But the action comes
too late for the many residents of east Oak Park whose trees have been ravaged.
The tragedy is that many of these irrevocably disfigured trees could have been
saved if someone at Village Hall would have listened sooner, and if those in
charge would have known what they were doing.
Inside
Report, editorial, page 2, Wednesday Journal
Can't see the
forest for the tree-trimmers
Citizens Tree
Rescue and other concerned citizens took on the village and public works the
past couple of weeks, denouncing the ironhanded, aggressive tree trimming on
blocks between Austin Boulevard and Oak Park Avenue, South Boulevard and Madison
Street.
Last Wednesday,
landscape professionals, village government officials, and citizens toured the
trimmed areas, and all agree the trees had been cut too severely. In some cases,
branches up to 20 feet from the ground were removed, leaving unadorned trunks
at the bottom and tufts of foliage at the top.
Among those
in attendance were: Village president Barbara Furlong, assistant village manager
M. Ray Wiggins, pubic works director Joe Euclide, director of forestry Jim Semelka,
a representative from A&B Landscaping, landscape architects Mark Finger and
Karen Heller from Carol Yetken Associates, Kathryn Jonas of Citizens Tree Rescue,
and urban forester Chuck Stewart.
As of Thursday,
the trees on the 100 and 200 blocks of Grove Street were pruned to new guidelines,
and Kenilworth, Clinton, Home Marion, and Maple will be trimmed less severely
as well. The village's pruning standards will be reviewed before the next pruning
season.
Fifty-two
square blocks of trees were trimmed before the meeting, and the lower branches
have been irreversibly removed.
Inside
Report, editorial, Wednesday Journal, July 4, 2001
Yetken's plea saves a tree at Julian
An elm tree near the about-to-be-leveled Percy Julian Junior High building was
saved last week thanks to the irrefutable logic of Carol Yetken, landscape architect.
The district's original plan saved one elm. Yetken's new plan saves two.
Throughways
for the construction site had been shifted to save a crabapple tree on the west
end of the site. Yetken said, "The crab is a small, younger, less quality tree."
Yetken
said that there are so few of the large trees left, and the corner of Ridgeland
Avenue and Washington Boulevard houses two of the elms.
Her plea came in the nick of time: One of the elms was slated for removal Thursday
morning. "They were saved by the skin of their bark," said Gary Johnson of Citizens
Tree Rescue, an ad hoc group dedicated to saving Oak Park trees. The Oak Park
Elementary School District 97 school board and Superintendent Jack Fagan were
convinced. The next day, they worked out a revised plan so trucks will enter
the Julian site from Washington Boulevard, and no elms will be removed from
site entry. The smaller crabapple tree was cut down.
Yetken's
next project? Saving the Linden trees in front of the about-to-be-leveled library
site.